Welcome to my blog website, where I share my experiences, insights, and knowledge in in the field of Cloud & DevSecOps.
Recent Blogs
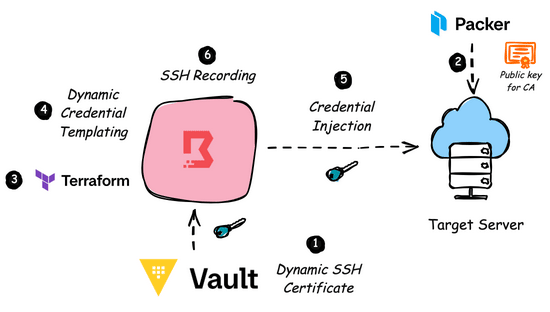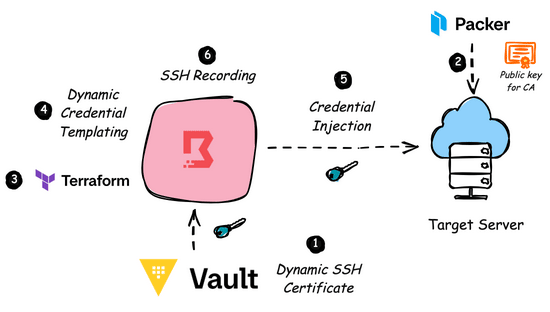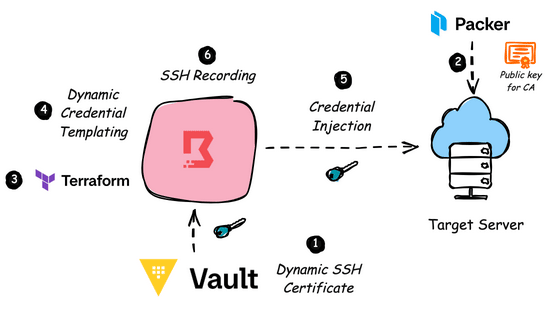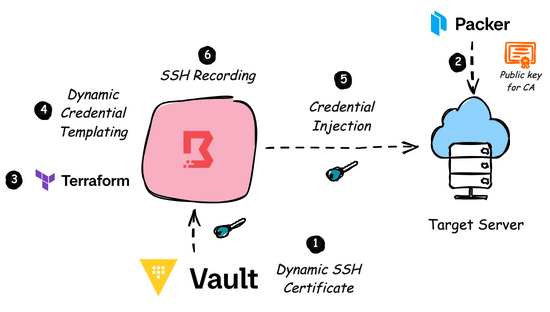
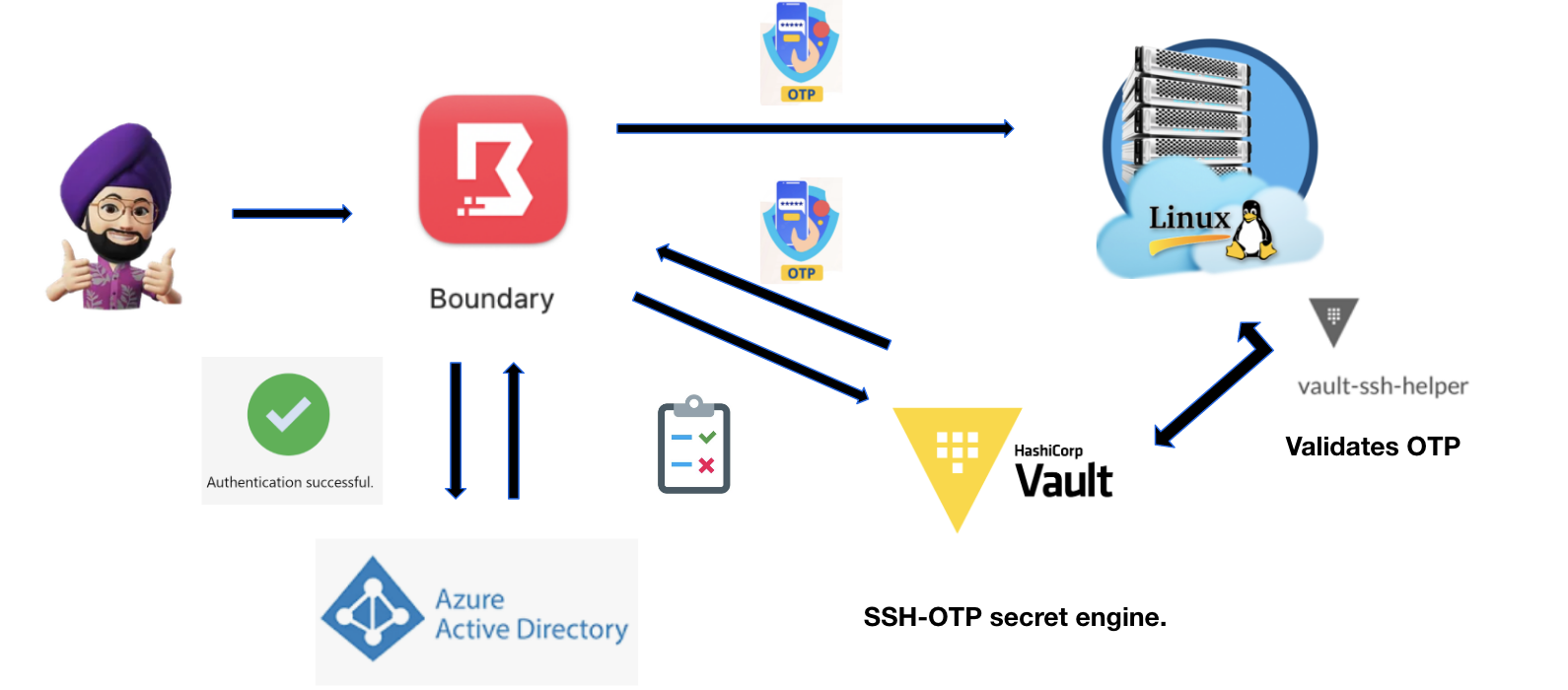
Empowering Credential Injection at scale using HashiCorp Boundary
In cloud environments, if we have to move towards zero trust security philosophy, we need to bring HashCorp Boundary and Vault integration into play.
Boundary is an identity-aware proxy solution that provides a simple, secure way to access hosts and critical systems on your network and Vault is HashiCorp’s comprehensive secrets management solution. The typical workflow would be like:
The Boundary user, through CLI/Desktop app, authenticates to Boundary Control Plane using an identity provider.
read more
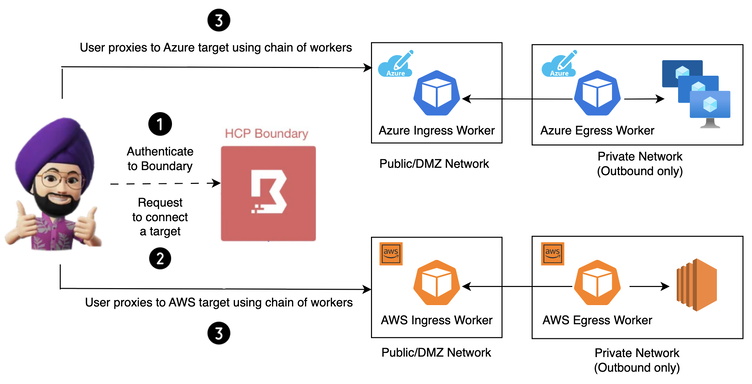
Solving PAM in hybrid environment using multi-hop sessions with HCP Boundary
Does your organisation has strict networking constraints like resources residing in private network having only outbound access? In this article, I am going to highlight and demo the solution using multi-hop sessions with HCP Boundary and how you can access resources in private networks across Azure and AWS.
read more
Avoid resource sprawling using dynamic credential templating in Hashicorp Boundary
Have you faced a challenge of maintaining user specific targets and credential libraries in Boundary and eventually ended up in a resource sprawl. In this article, I am going to highlight the solution using dynamic credential templating in Hashicorp Boundary which will help in avoiding resource sprawl.
read more